 Set Up Okta OIDC SSO for Kestra
Set Up Okta OIDC SSO for Kestra
Set up Okta OIDC SSO
This guide provides step-by-step instructions to configure OpenID Connect (OIDC) authentication using Okta and link it to Kestra Enterprise for Single Sign-On (SSO).
Prerequisites
- Okta Developer Account: Ensure you have an Okta Developer Account or Organization.
- Administrator Access: You need sufficient permissions to configure Identity Platform and manage identity providers.
- Kestra Enterprise Edition: Kestra SSO is available only in the Enterprise Edition.
This guide covers setup with Okta from a high level, refer to the Okta OIDC setup documentation for more details.
Step 1: Create an App Integration
Log in to your Okta account and select Applications from the left side menu.
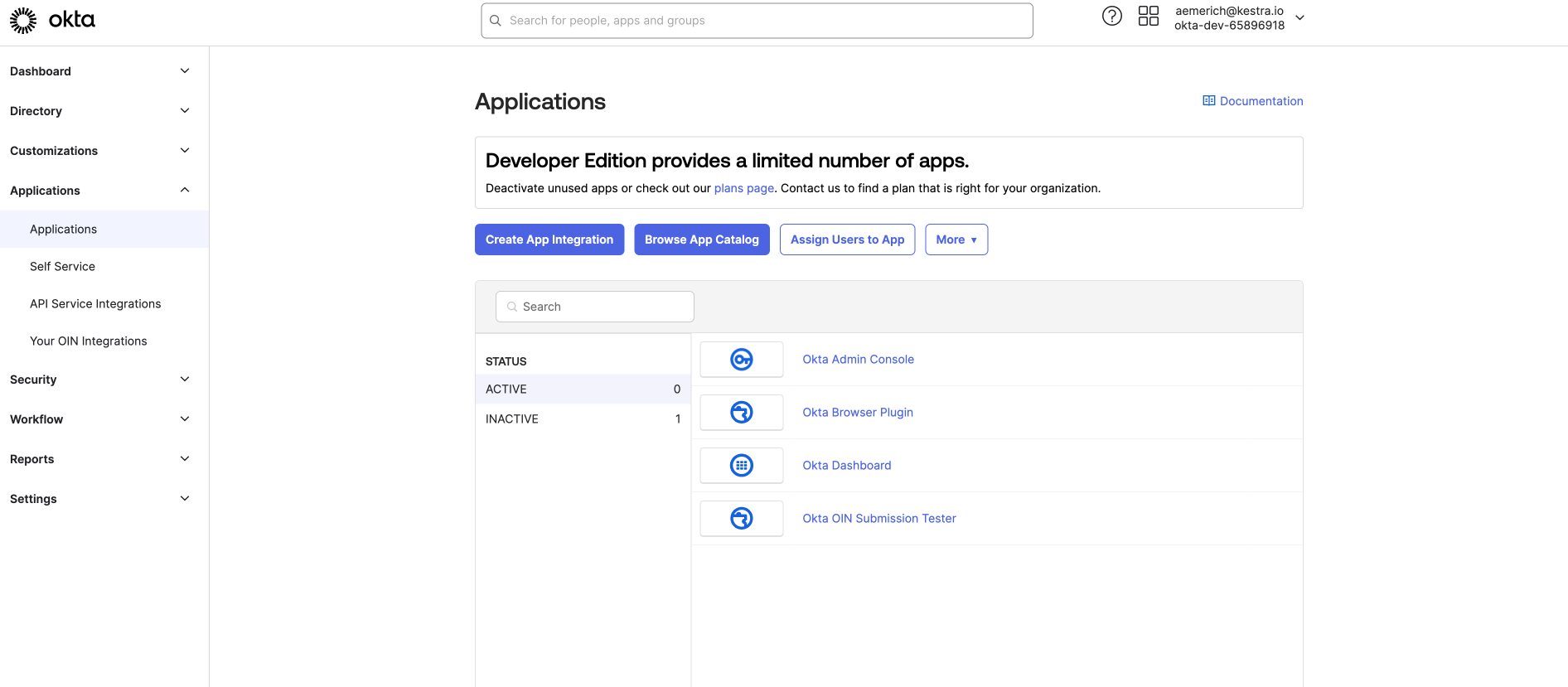
Next, select Create App Integration, select OIDC - OpenID Connect as the sign-in method and Web Application as the application type. Select Next, and you will be taken to configure the general settings of the new web app integration.
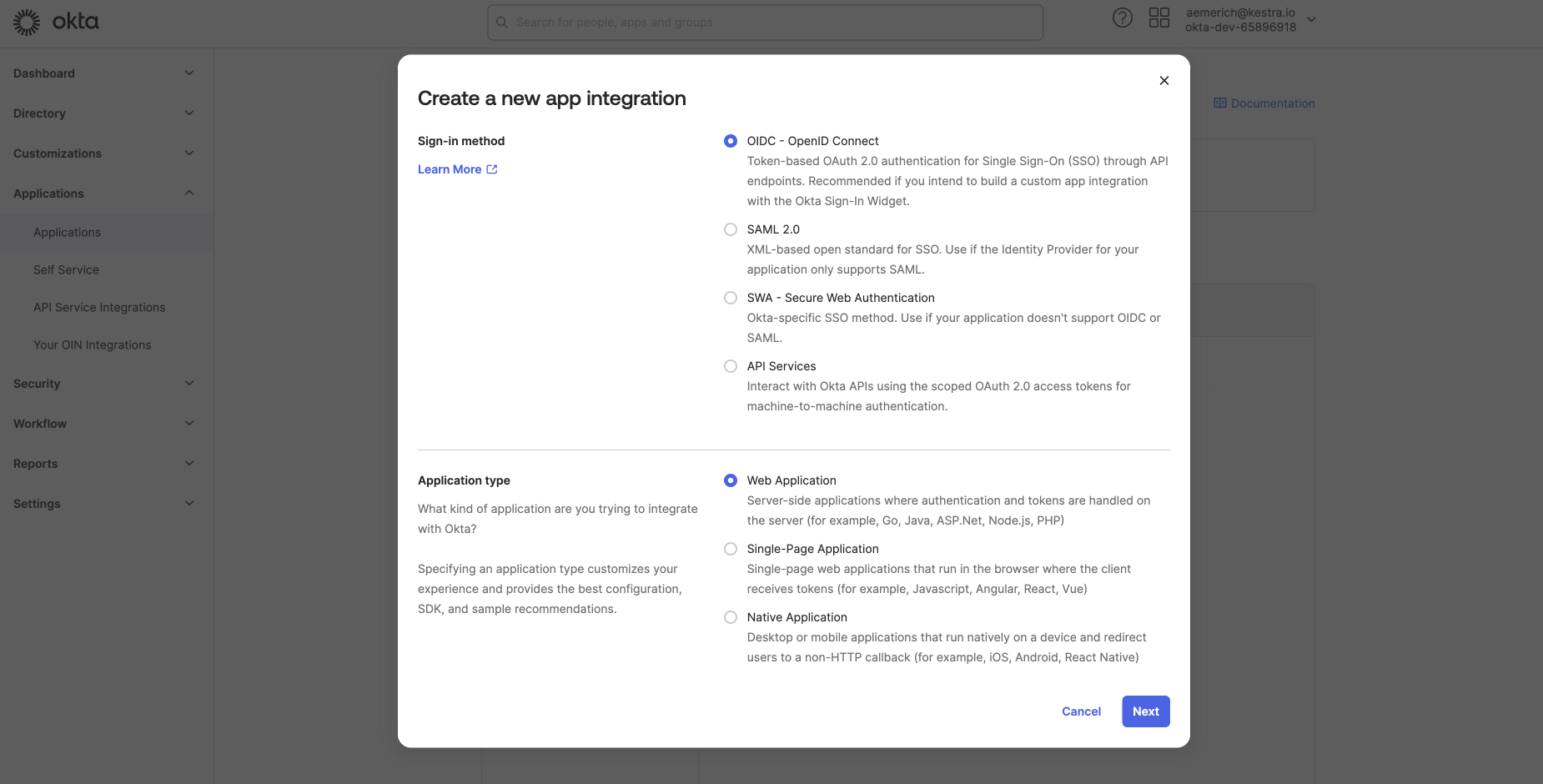
Step 2: Configure the web app integration
In the General Settings, give your App integration a name and set your grant type. For this example, we are using Authorization Code. You can open Advanced Settings to configure more sensitive grants. Okta has several direct-auth API grants, such as OTP, OOB, MFA OTP, and MFA OOB that you can select only if necessary.
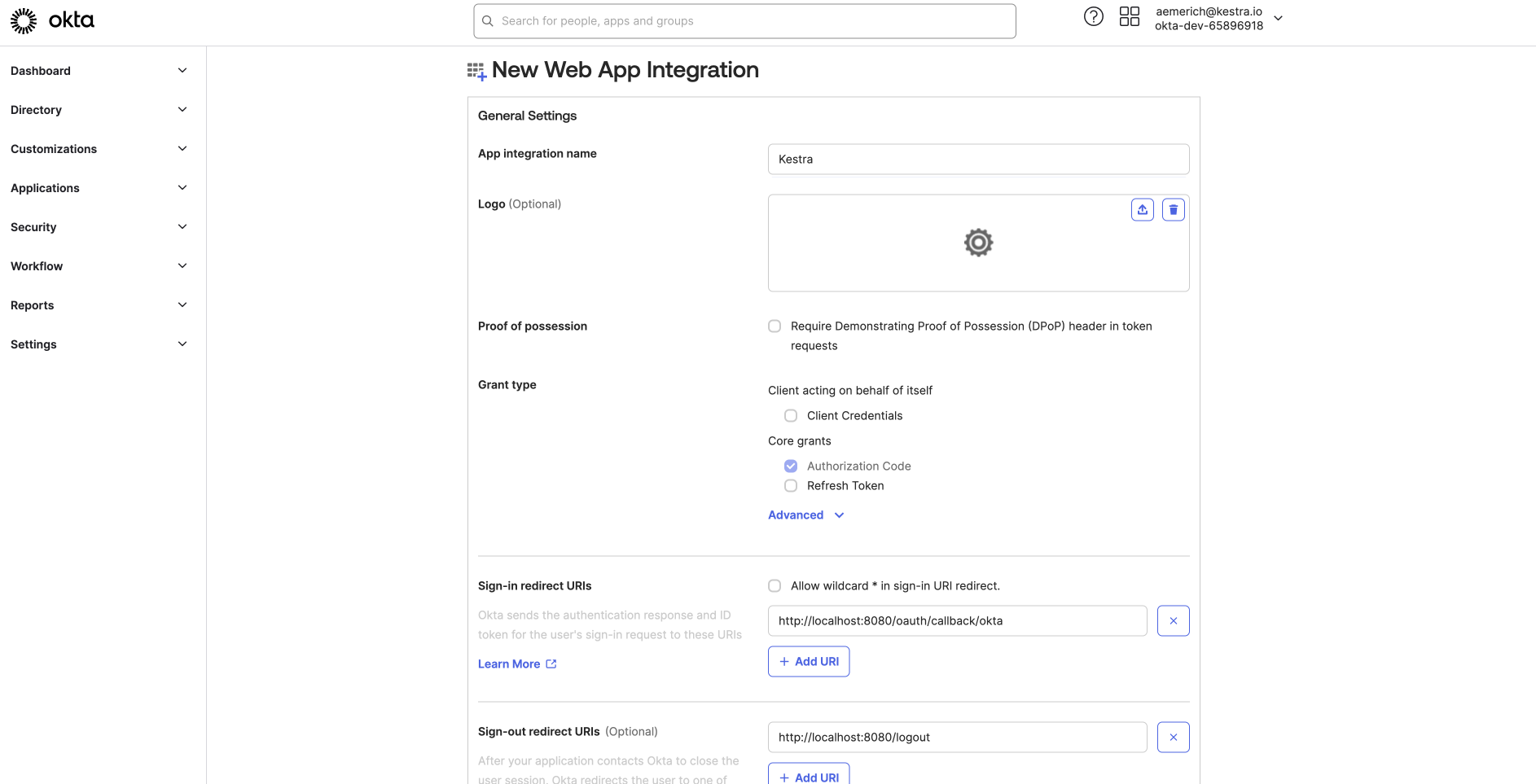
Here, you also set the Sign-in redirect URIs and Sign-out redirect URIs for your App integration. For this example connecting to Kestra, we set a Sign-in redirect URI as http://localhost:8080/oauth/callback/okta and sign-out as http://localhost:8080/logout, but you can customize this to your environment.
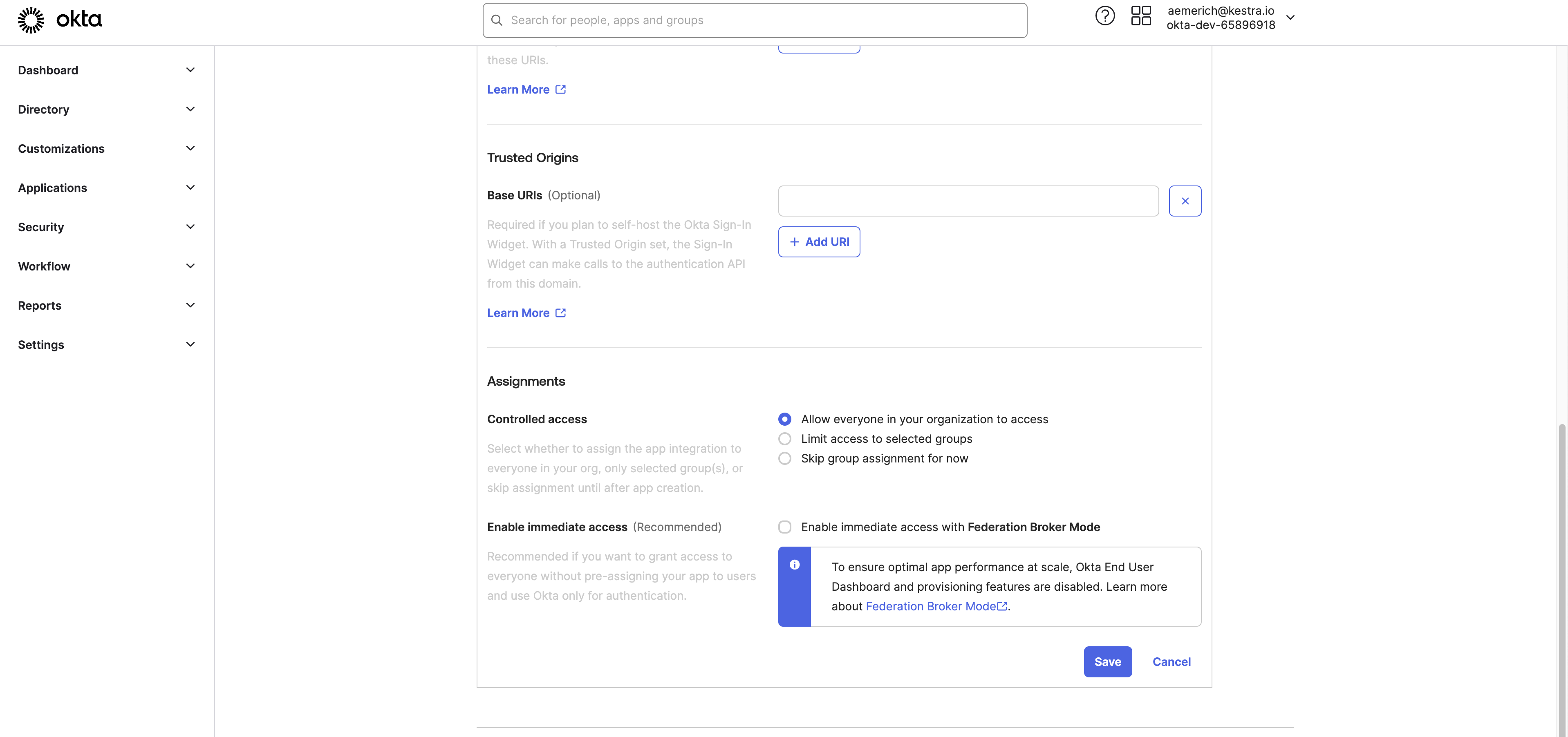
Further down the page, you can configure optional Trusted Origins, and then choose the Assignments and the access settings for the App integration.
We’ll set the access to everyone in the organization, but you can set stricter access to only certain selected groups or skip for now. Lastly, we uncheck the setting to enable immediate access with Federation Broker Mode because we will give manual app access for this basic example. Finally, hit Save.
Step 3: Add test user to Okta app integration
To create a test user in your Okta Directory to test your app integration, in your Okta Admin Dashboard, navigate to Directory > People. Select Add Person.
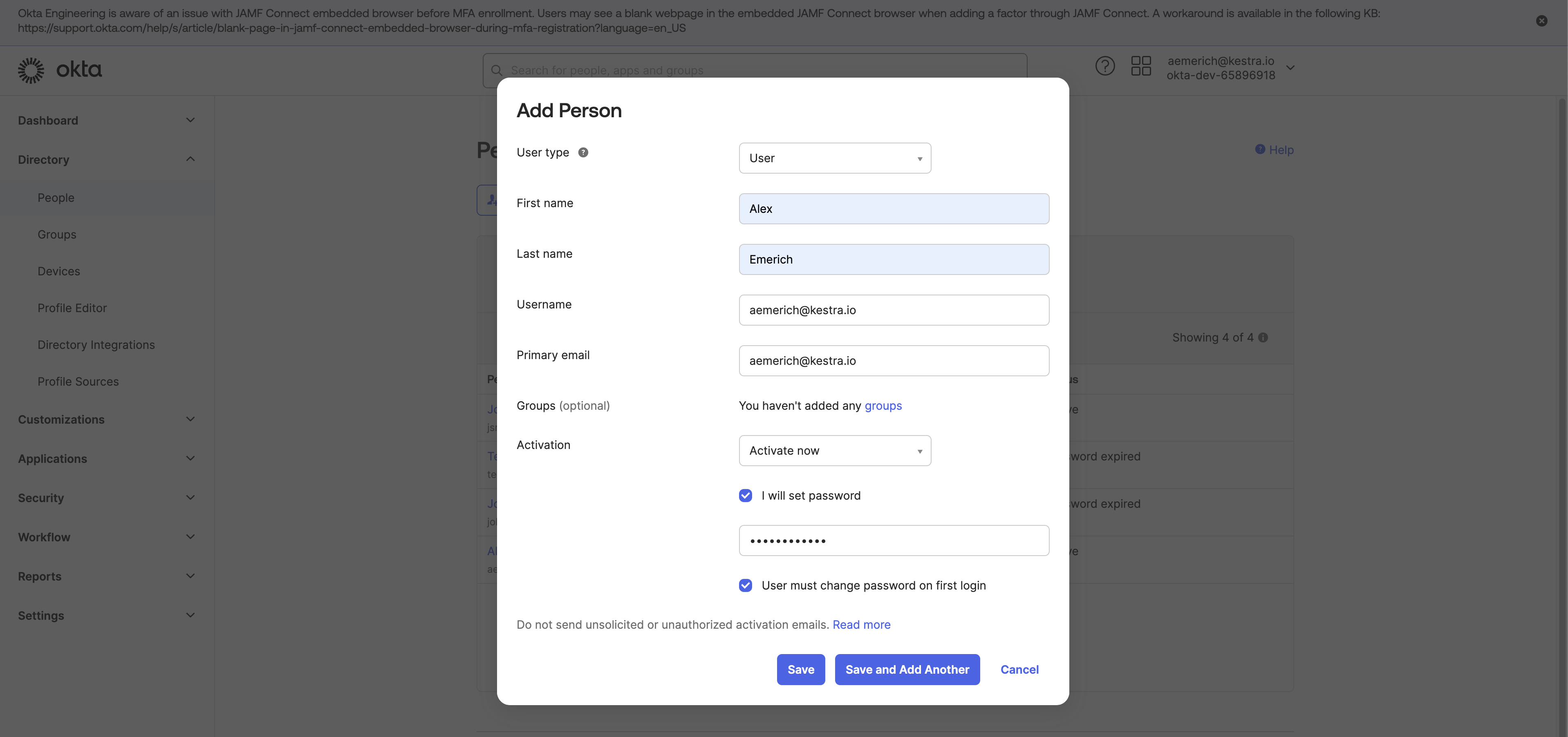
Enter user test details, including a password, and save the test user.
In the Directory, select the new user, and navigate to the Applications tab for the user and choose Assign Applications.
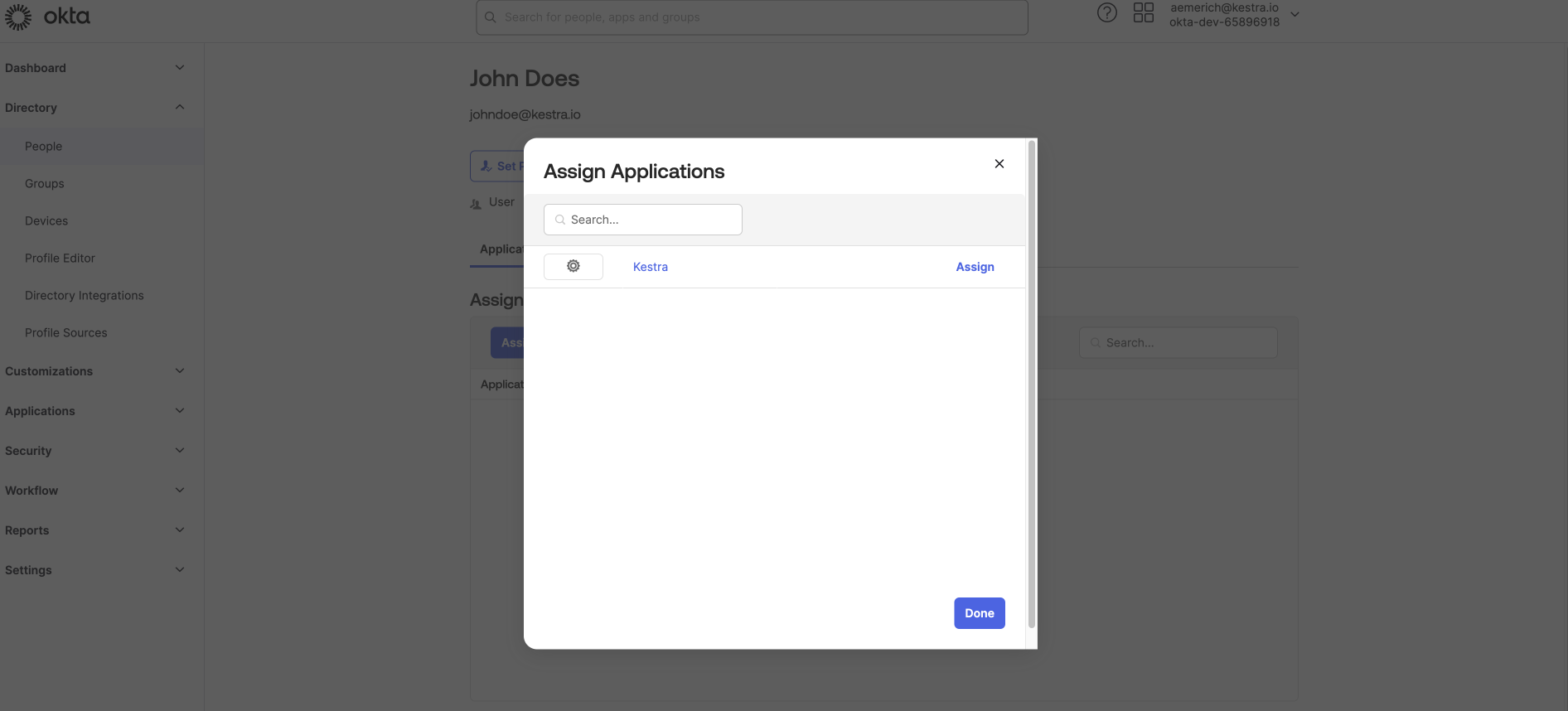
Select the Kestra application name you created and enter the added details for the user and hit Save.
Step 4: Connect to Kestra
Now that Okta is set up as an OIDC provider, we need to link it to Kestra. After saving your settings in the previous step, Okta will automatically redirect you to your integration. Here, you can collect your client credentials to connect to Kestra, Client ID and Client Secret.
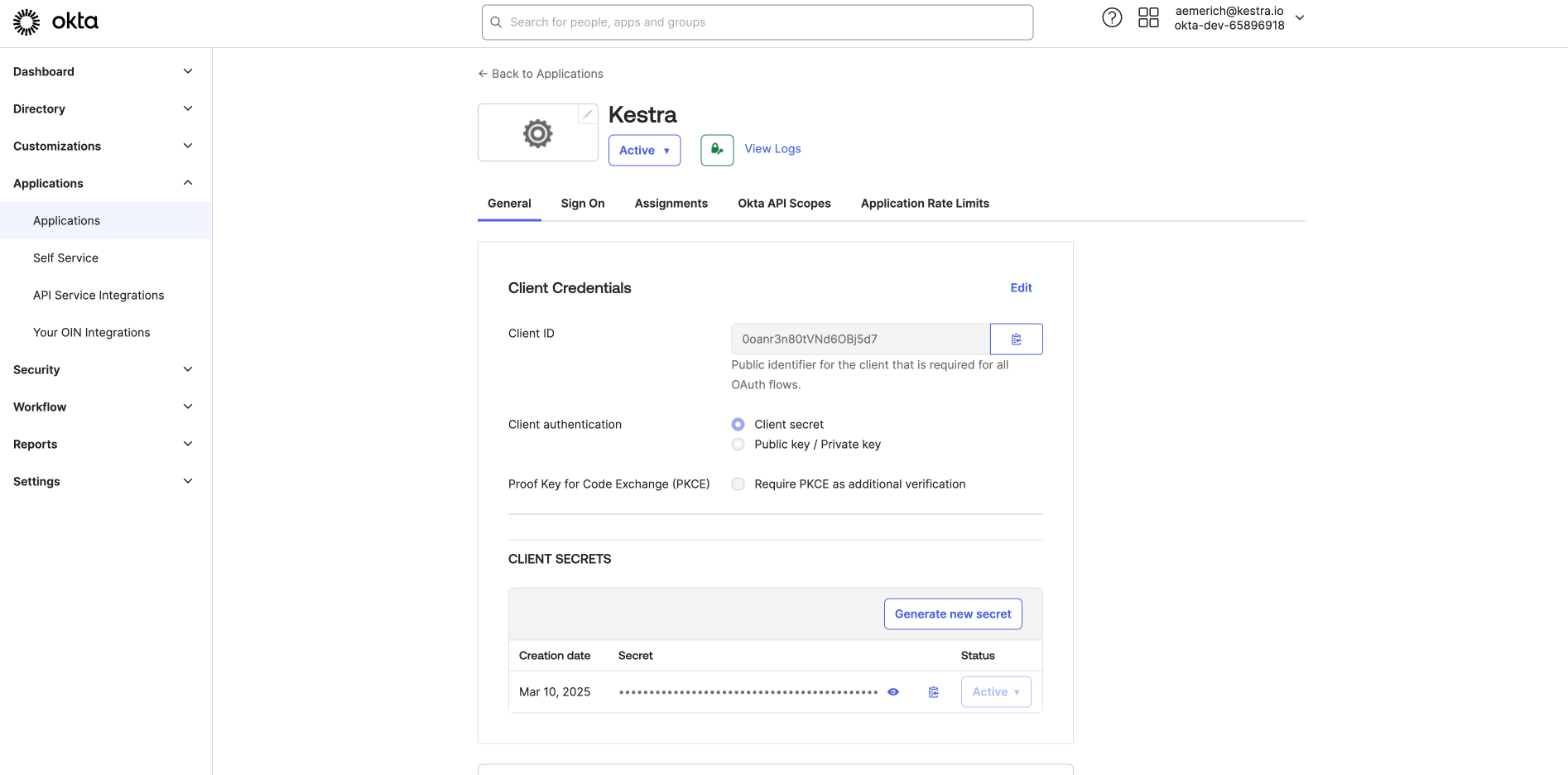
After copying your Client ID and Client Secret, switch from the General tab to the Sign On tab. Here, you can configure your OpenID Connect ID Token. For this example, we will edit the issuer from Dynamic to our Okta URL. Click Save and copy the URL to be used in our Kestra configuration along with the Client ID and Client Secret.
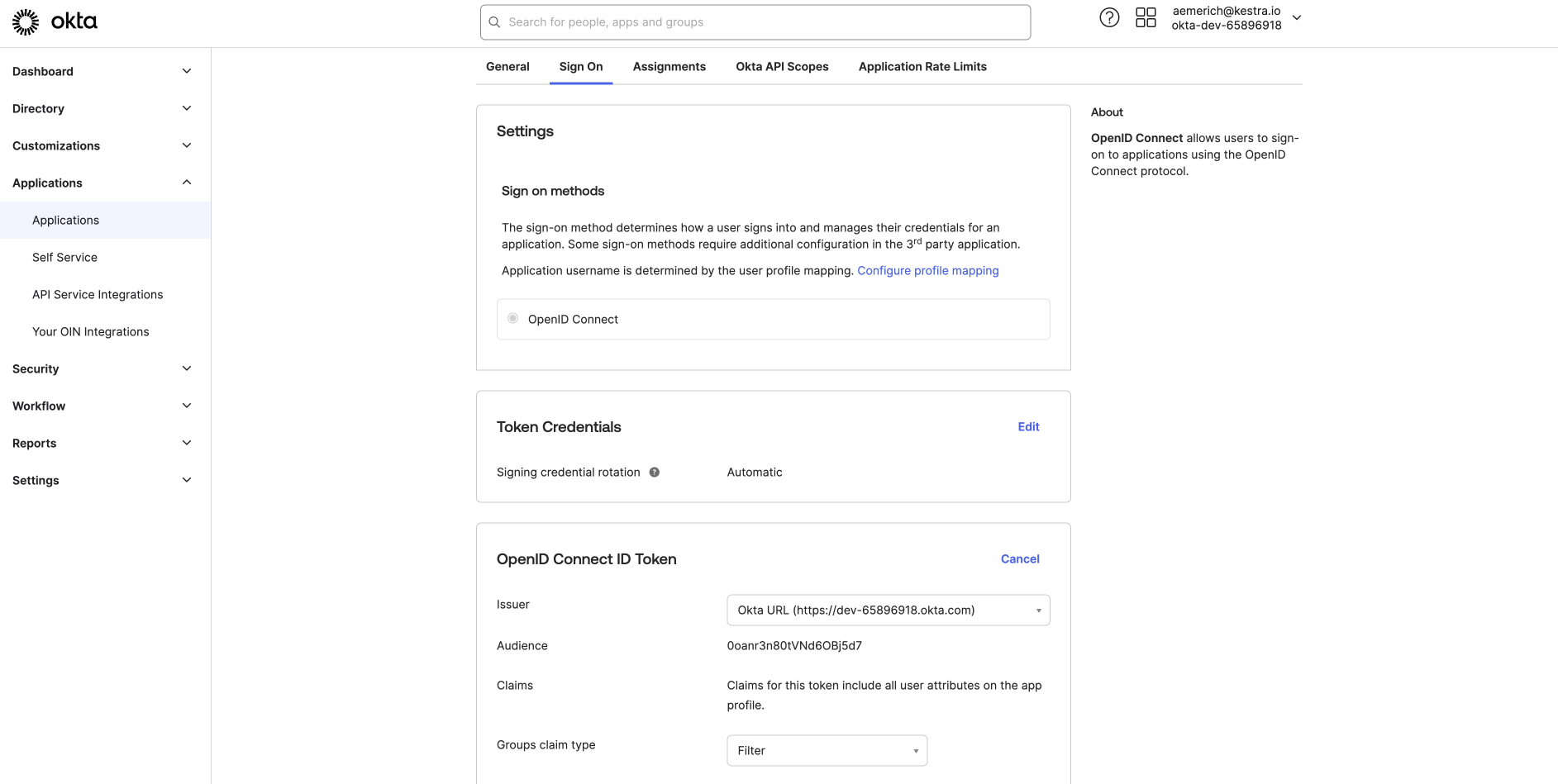
-
Navigate to the Kestra Configuration File:
- Locate the Kestra configuration file.
-
Add the OIDC Settings:
- Add the following configuration to enable Okta as an OIDC provider for Kestra:
micronaut: security: oauth2: enabled: true clients: okta: client-id: "{{ clientId }}" client-secret: "{{ clientSecret }}" openid: issuer: 'https://<your-domain-id>.okta.com'- Replace
clientIdandclientSecretwith the values copied from the Okta App integration. - Replace
issuerwith your issuer URL from Application’s sign on settings from before. - Restart Kestra to apply the changes and log in.
On restart, you will now see Okta as an available login method.

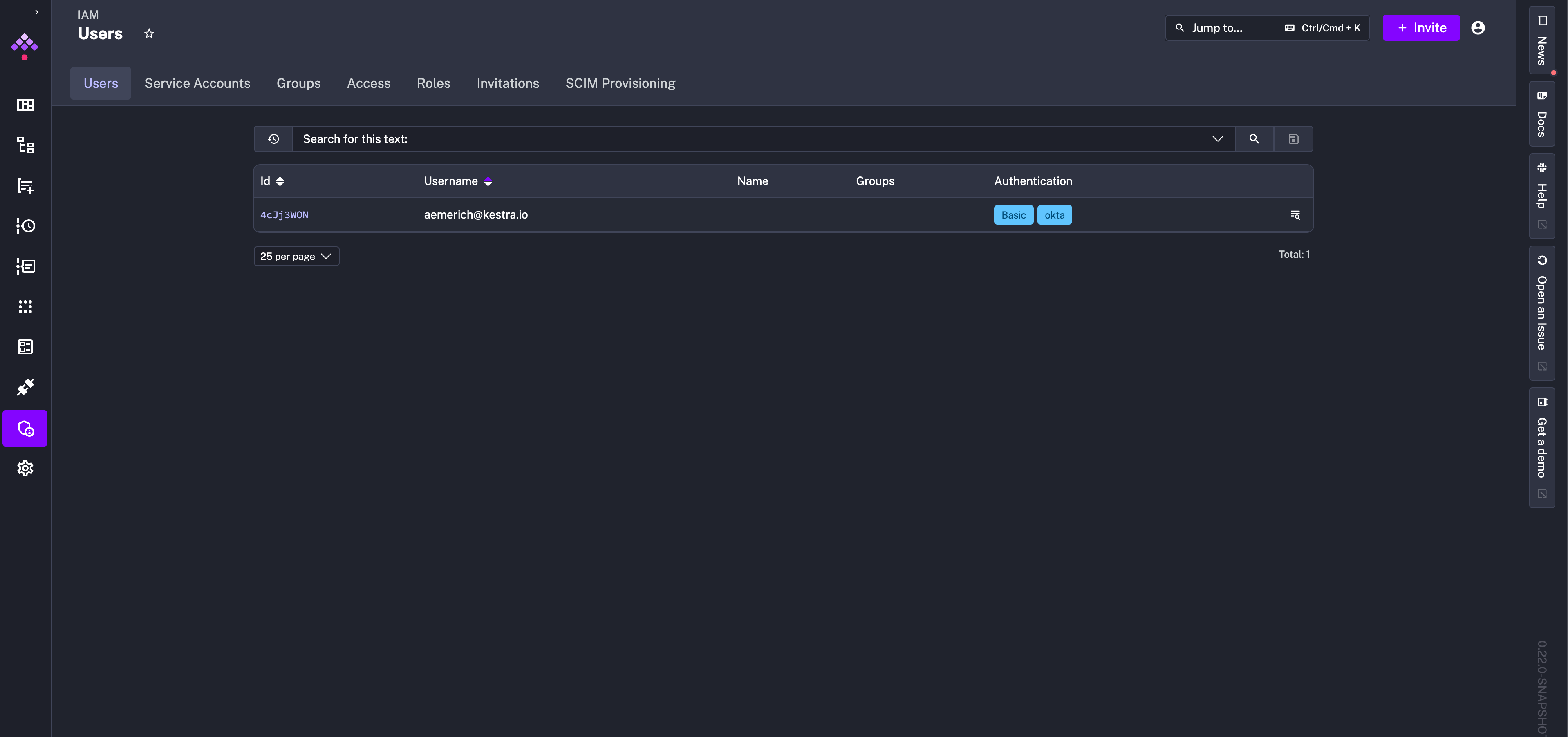
After logging in with the created user, navigate to the Administration > IAM tab, and you can see in the Users tab that the user can sign in with basic authentication as well as Okta.
Was this page helpful?