 Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC)
Available on:
How to manage access and permissions to your instance.
Overview
Kestra Enterprise supports Role-Based Access Control (RBAC), allowing you to manage access to workflows and resources by assigning Roles to Users, Groups, and Service Accounts.
The image below shows the relationship between Users, Groups, Service Accounts, Roles, and Bindings (visible on the Access page in the UI).
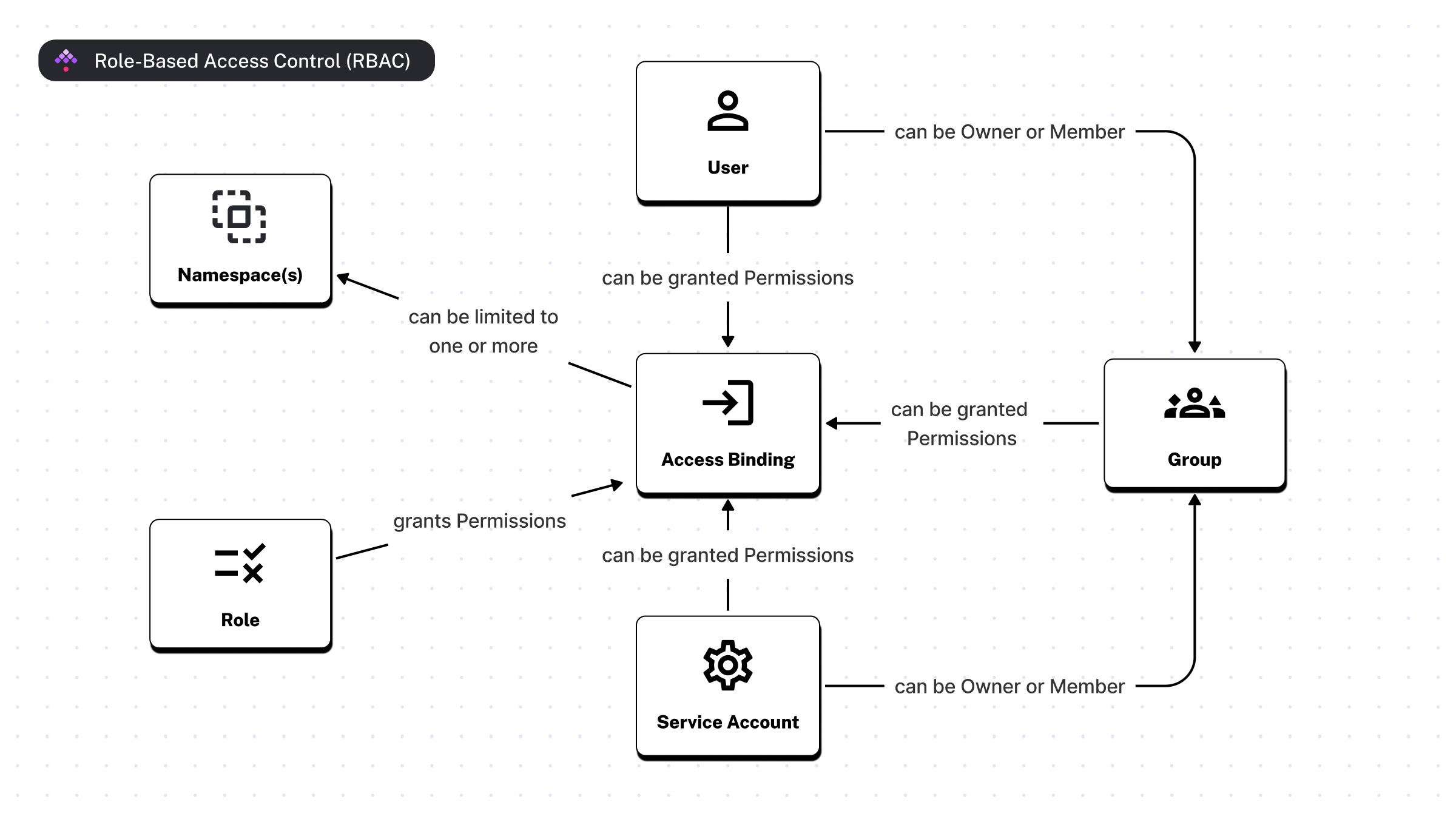
Roles and Bindings
A Role is a collection of permissions that can be assigned to Users, Service Accounts, or Groups.
These permissions are defined by a combination of a Permission (e.g., FLOWS) and an Action (
e.g., CREATE).
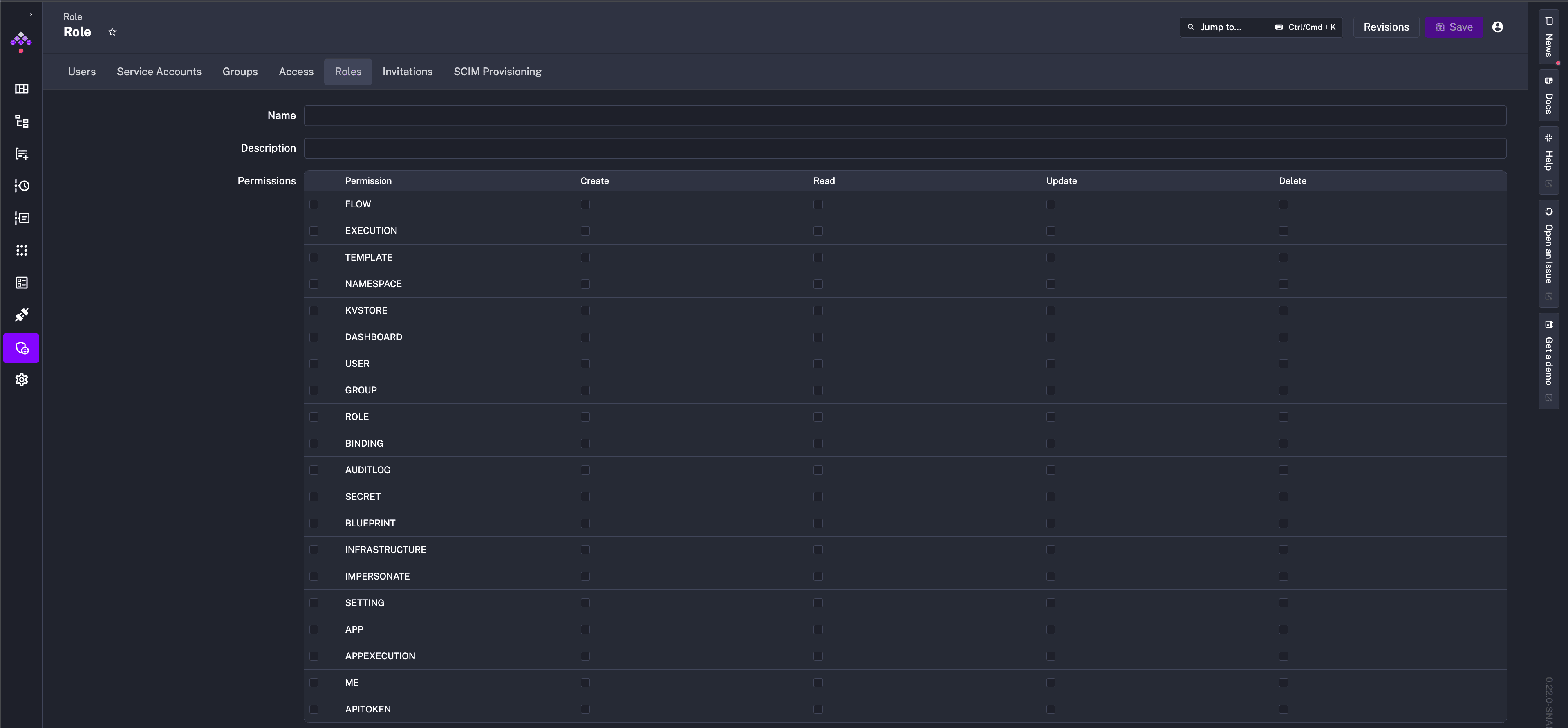
Permissions
A Permission is a resource that can be accessed by a User or Group. Supported Permissions:
FLOWEXECUTIONTEMPLATENAMESPACEKVSTOREDASHBOARDUSERGROUPROLEBINDINGAUDITLOGSECRETBLUEPRINTIMPERSONATESETTINGAPPAPPEXECUTIONMEAPITOKENSERVICE_ACCOUNTINVITATIONTENANT_ACCESSGROUP_MEMBERSHIP
The ME and APITOKEN are removed in Kestra 0.24
Actions
An Action is a specific operation that can be performed on a Permission. Supported Actions:
CREATEREADUPDATEDELETE
Currently supported roles
Currently, Kestra only creates an Admin role by default. That role grants full access to all resources.
Apart from that, you can create additional Roles with custom permission combinations. You can create roles and select the permissions and actions in the IAM - Roles tab.
Super Admin and admin
Kestra provides two roles for managing your instance: super admin and admin.
- Super Admin is a user type with elevated privileges for global control
- Admin is a customizable role that grants full access to all resources (scoped to a tenant if multi-tenancy is enabled).
Super Admin
Without any Role or Binding, Super Admin has access to manage tenants, users, roles, and groups within a Kestra Enterprise instance.
Was this page helpful?